Computer Penetration Tester with nearly 5 years of experience in assessing, testing, and fortifying digital and physical security landscapes.
My priority is to perform penetration testing with a high degree of vulnerability detection accuracy while demonstrating vulnerability impact through targeted exploitation. More importantly, I focus on delivering high quality reports that I can explain to all audience levels.













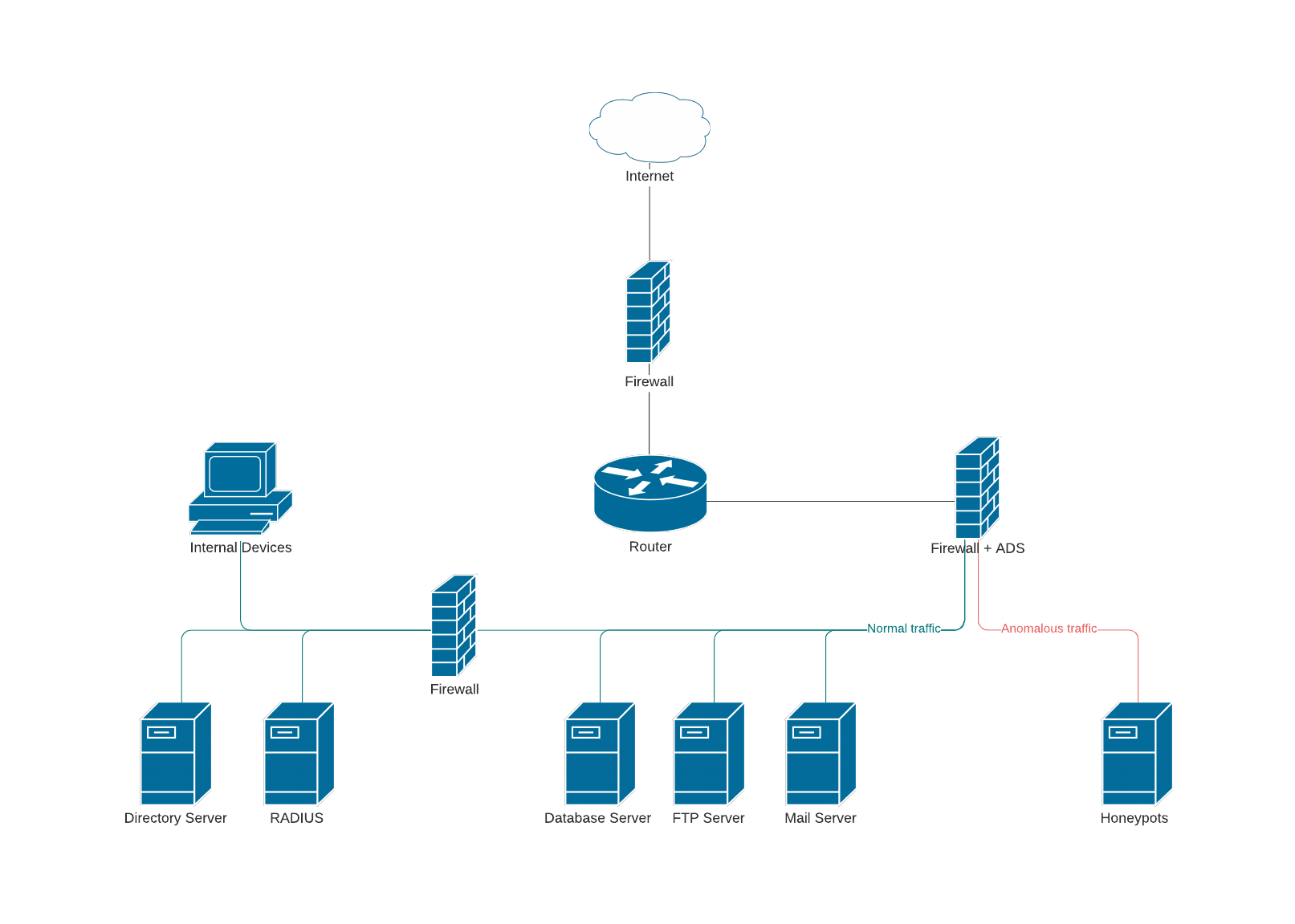 The primary focus in my five years of penetration testing have been in testing at the network level. My background in network testing covers both the external and internal network perspective, particularly when Active Directory is involved. Many of the certifications I hold cover network and Active Directory testing like the OSEP, OSCP, and CRTP.
The primary focus in my five years of penetration testing have been in testing at the network level. My background in network testing covers both the external and internal network perspective, particularly when Active Directory is involved. Many of the certifications I hold cover network and Active Directory testing like the OSEP, OSCP, and CRTP.
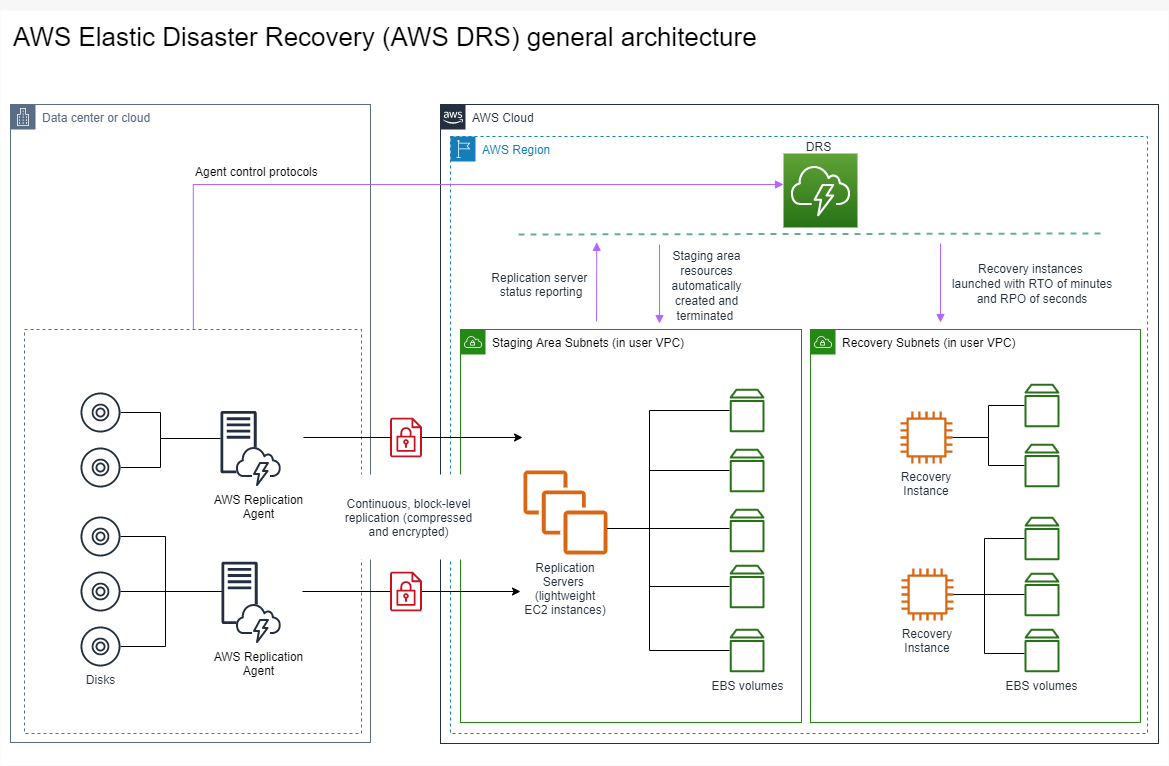 I’ve tested many cloud based environments in my tenure as a penetration testing with my primary focus in AWS and Azure. The goal of the cloud assessments I’ve performed is to determine if an attacker can escalate privileges in the cloud by abusing the permission set of a common account. I’ve obtained a few AWS certifications like the AWS CCP and AWS CSA(A) to validate my understanding of the cloud for this testing format.
I’ve tested many cloud based environments in my tenure as a penetration testing with my primary focus in AWS and Azure. The goal of the cloud assessments I’ve performed is to determine if an attacker can escalate privileges in the cloud by abusing the permission set of a common account. I’ve obtained a few AWS certifications like the AWS CCP and AWS CSA(A) to validate my understanding of the cloud for this testing format.
 While working as a penetration tester, I’ve gotten the opportunity to train and test on physical side of security. Physical security penetration testing can vary widely in scope and purpose, but generally speaking it will involve testing the effectiveness of physical security controls via covert entry and social engineering. I am currently in the process of studying for the Red Team Alliance (RTA) Covert Entry Associate (CEA) certification after taking the RTA Covert Method of Entry (CMoE) course.
While working as a penetration tester, I’ve gotten the opportunity to train and test on physical side of security. Physical security penetration testing can vary widely in scope and purpose, but generally speaking it will involve testing the effectiveness of physical security controls via covert entry and social engineering. I am currently in the process of studying for the Red Team Alliance (RTA) Covert Entry Associate (CEA) certification after taking the RTA Covert Method of Entry (CMoE) course.
 Wireless network testing is often combined with physical security testing and on-site social engineering since it often requires the tester to be physically present at the target organization. I have conducted a handful of wireless penetration tests and assessments alongside physical security assessments as another means to break into the target organization’s network by searching for security misconfiguration in the wireless network from a nearby location.
Wireless network testing is often combined with physical security testing and on-site social engineering since it often requires the tester to be physically present at the target organization. I have conducted a handful of wireless penetration tests and assessments alongside physical security assessments as another means to break into the target organization’s network by searching for security misconfiguration in the wireless network from a nearby location.
 Just behind network penetration testing, social engineering is where I have the second most experience. I have conducted numerous phishing, vishing, and on-site impersonation social engineering tests. Additionally, I have a background setting up the infrastructure to support these engagements and bypass some spam detection on phishing engagements.
Just behind network penetration testing, social engineering is where I have the second most experience. I have conducted numerous phishing, vishing, and on-site impersonation social engineering tests. Additionally, I have a background setting up the infrastructure to support these engagements and bypass some spam detection on phishing engagements.

October 24th, 2024